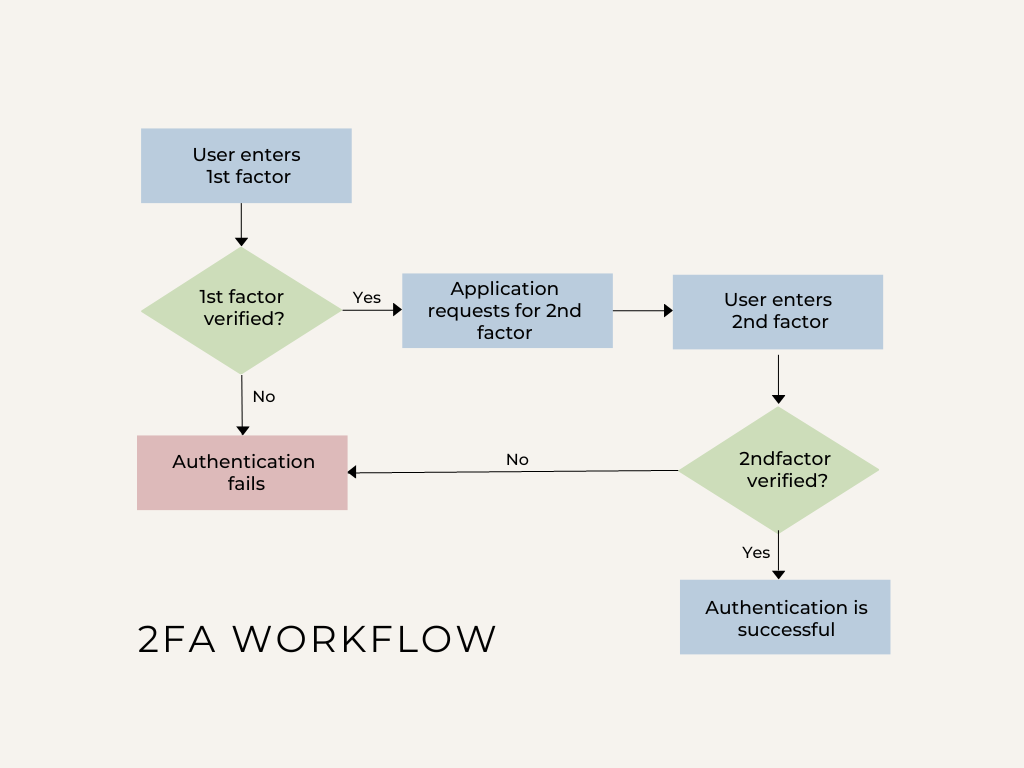
Securing your SSH connections is paramount, especially once dealing with delicate information. This station delves into enhancing Paramiko’s SSH capabilities by implementing robust multi-cause authentication utilizing some password and cardinal-based methods. We’ll research however to harvester these approaches for a much unafraid transportation to distant servers.
Strengthening SSH with Paramiko: A Multi-Cause Attack
Paramiko, a almighty Python room for interacting with SSH, gives the instauration for unafraid distant entree. Nevertheless, relying solely connected passwords is dangerous. By integrating cardinal-based authentication alongside password authentication, we make a multi-cause authentication scheme, importantly bettering the safety posture of our purposes. This layered attack makes unauthorized entree exponentially much hard, defending your invaluable information and infrastructure. This usher focuses connected applicable implementation, emphasizing safety champion practices.
Leveraging SSH Keys for Enhanced Safety
SSH keys message a superior alternate to password-lone authentication. Alternatively of relying connected easy guessed oregon compromised passwords, cardinal-based authentication makes use of a brace of cryptographic keys: a backstage cardinal (stored concealed) and a national cardinal (shared with the server). Once connecting, Paramiko makes use of the backstage cardinal to be individuality to the server, without always transmitting the existent password. This method is cold much resistant to brute-unit assaults and unauthorized entree. Implementing SSH keys frequently includes producing a cardinal brace utilizing instruments similar ssh-keygen and past securely distributing the national cardinal to the authorized server. Larn much astir SSH keys present.
Combining Password and Cardinal Authentication successful Paramiko
Piece cardinal-based authentication is importantly much unafraid, it’s not ever applicable to trust solely connected this method. Integrating password authentication arsenic a fallback increases usability without compromising safety. This mixed attack requires cautious dealing with of some authentication methods inside the Paramiko model. If the cardinal-based authentication fails, the codification should gracefully autumn backmost to password-based authentication, but lone last verifying the cardinal’s integrity. This prevents a possible azygous component of nonaccomplishment and ensures accessibility equal successful conditions wherever cardinal-based authentication mightiness temporarily neglect.
Applicable Implementation: A Paramiko Illustration
The pursuing illustration demonstrates a basal implementation of this dual authentication attack successful Python utilizing Paramiko. Line that mistake dealing with and much robust safety checks are important successful a exhibition situation.
import paramiko def connect_with_multi_factor(hostname, username, password, key_filename): attempt: cardinal = paramiko.RSAKey.from_private_key_file(key_filename) case = paramiko.SSHClient() case.set_missing_host_key_policy(paramiko.AutoAddPolicy()) case.link(hostname, username=username, pkey=cardinal) instrument case but paramiko.AuthenticationException: attempt: case = paramiko.SSHClient() case.set_missing_host_key_policy(paramiko.AutoAddPolicy()) case.link(hostname, username=username, password=password) instrument case but Objection arsenic e: mark(f"Authentication failed: {e}") instrument No Illustration utilization: case = connect_with_multi_factor("your_server_ip", "your_username", "your_password", "way/to/your/private_key") if case: mark("Transportation palmy!") ... your codification to work together with the server ... case.adjacent()
Retrieve to regenerate placeholders with your existent server particulars and cardinal record way.
Champion Practices for Unafraid SSH Connections
Implementing multi-cause authentication is a important measure towards enhancing safety, but it’s not the lone measurement. Regularly updating Paramiko and your server’s working scheme is captious. Ever usage beardown passwords and defend your backstage keys diligently. See utilizing a unafraid cardinal direction scheme. Regularly audit your SSH entree logs for suspicious act. Publication much astir securing SSH present. This holistic attack, combining beardown authentication with proactive safety measures, importantly minimizes the hazard of unauthorized entree.
Choosing the Correct Cardinal Algorithm
Once producing your SSH keys, choice a robust algorithm similar RSA with a adequate cardinal dimension (astatine slightest 2048 bits). Debar utilizing weaker algorithms that are much susceptible to brute-unit assaults. Appropriate cardinal procreation and direction are cardinal to the safety of your SSH connections. Larn much astir RSA encryption.
By combining cardinal-based and password-based authentication, and pursuing champion practices, you tin dramatically better the safety of your SSH connections utilizing Paramiko. Retrieve to prioritize safety and regularly reappraisal your practices to act up of possible threats.
#1 Multi-Factor Authentication: Everything you Need to Know
#2 What is Multifactor Authentication? - Tools4ever
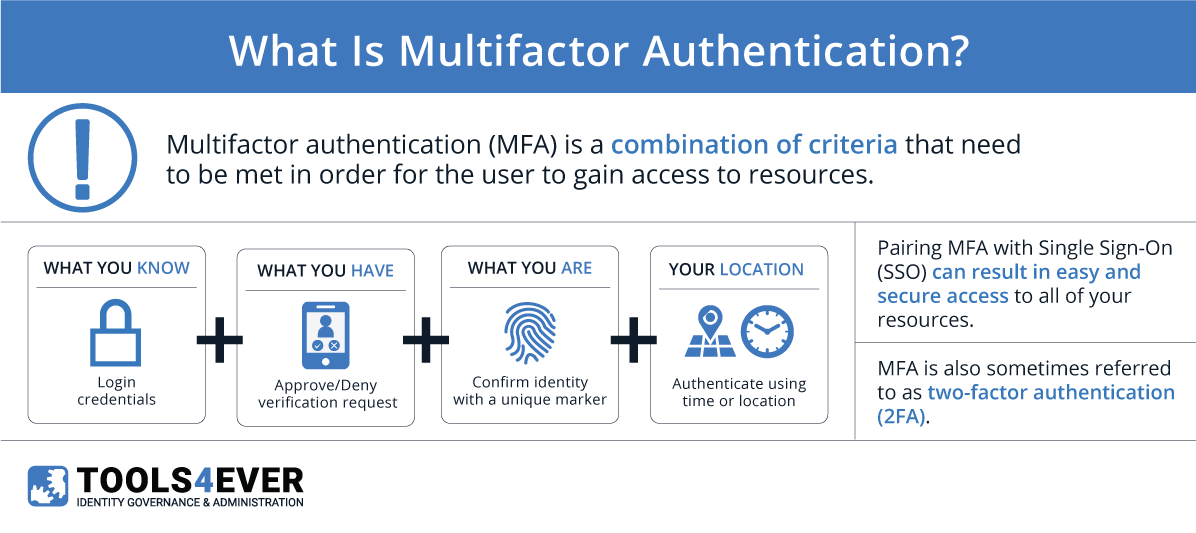
#3 What Is Multi Factor Authentication? | MFA Explained | Security Wiki
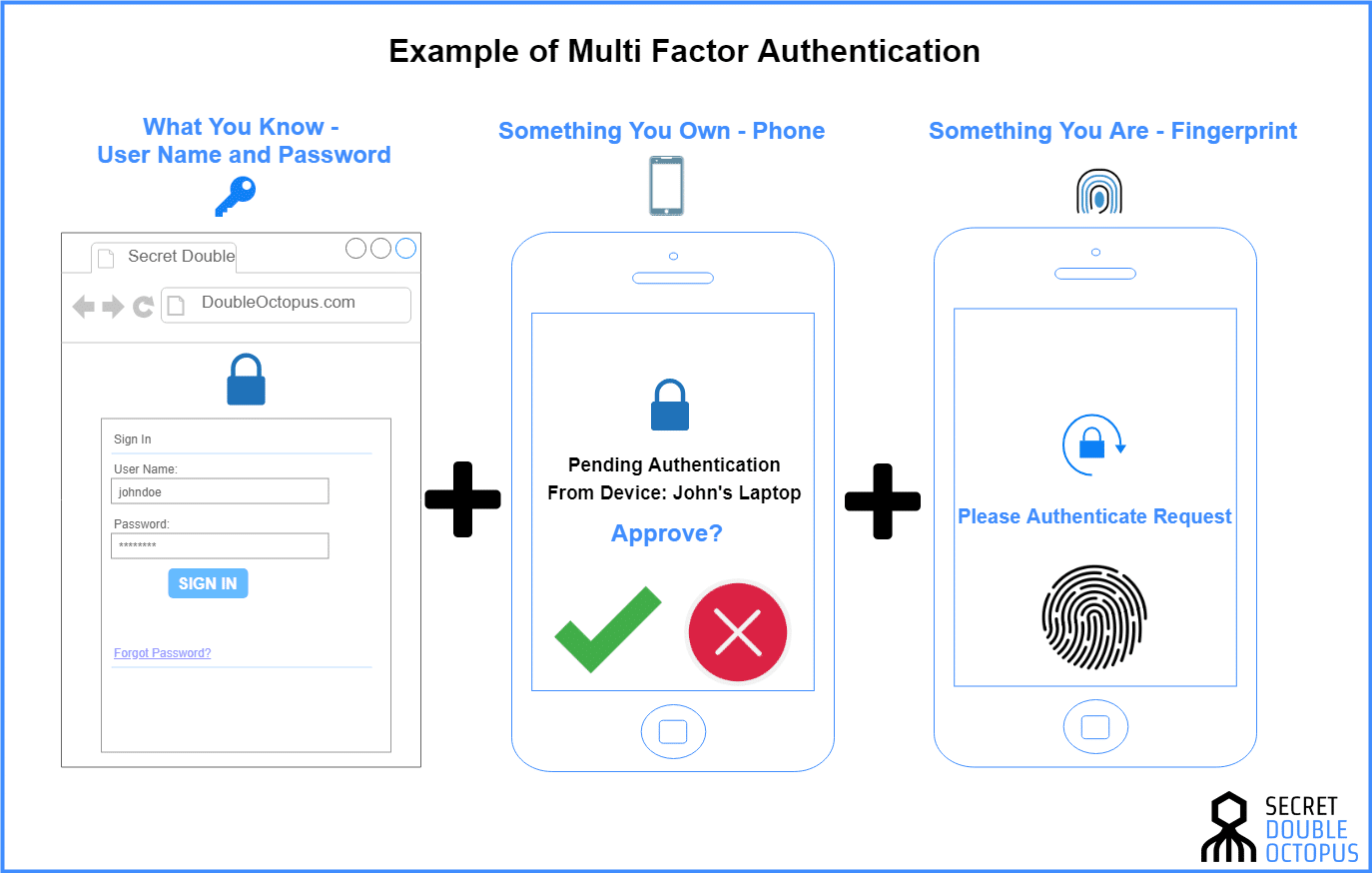
#4 Why Do You Need Password & Multi-Factor Authentication?
#5 Multi-Factor Authentication - How Does It Work? | Fraud.com

#6 Multi-Factor Authentication is Not an Option! | Data-Command
#7 Multi-Factor Authentication (MFA) Explained

#8 9 Best Practices for Multi-factor Authentication (MFA)