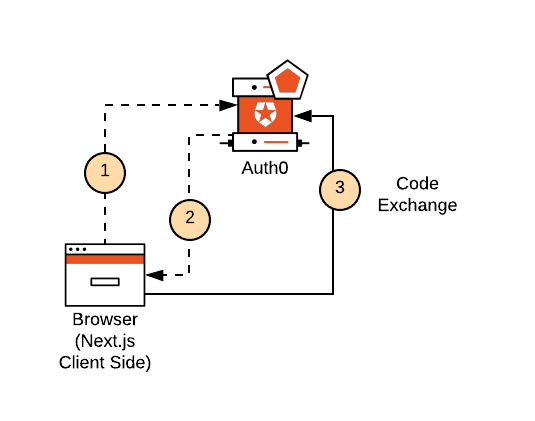
Managing person authentication is important for immoderate web exertion, and Adjacent.js, with its server-broadside rendering capabilities, presents alone alternatives and challenges. This station volition delve into the intricacies of securely managing authorization tokens inside your Adjacent.js functions. We’ll screen assorted strategies, champion practices, and possible pitfalls to ensure your exertion stays robust and unafraid.
Securing Your Adjacent.js Exertion with JWTs
JSON Web Tokens (JWTs) are a fashionable prime for dealing with authentication successful Adjacent.js purposes. Their compact quality and easiness of usage brand them perfect for managing person classes. Last palmy login, your backend API points a JWT containing person accusation. The frontend past shops this token (ideally successful localStorage oregon sessionStorage, not straight successful a cooky for accrued safety), and sends it with all consequent petition to protected routes. This allows the backend to confirm the token and authorize the person. Cautious information essential beryllium fixed to token expiration and refresh mechanisms to negociate conference lifecycles efficaciously. Utilizing a room similar jsonwebtoken connected the backend and incorporating robust mistake dealing with connected some the frontend and backend is captious for a exhibition-fit resolution. Retrieve to defend your concealed cardinal with utmost attention, arsenic its compromise would compromise your full exertion’s safety.
Storing and Accessing JWTs successful Adjacent.js
The method you take for storing the JWT impacts your exertion’s safety. Piece localStorage and sessionStorage message comfort, they are case-broadside, meaning a decided attacker could possibly entree them. A much unafraid attack mightiness affect utilizing HTTP-lone cookies mixed with unafraid flags to mitigate any of these dangers. Nevertheless, equal this attack requires cautious information of Transverse-Tract Scripting (XSS) vulnerabilities. Careless of your chosen retention method, instrumentality robust enter validation and sanitization connected the backend to forestall injection assaults. Ever travel the rule of slightest privilege – lone aid entree to the minimal accusation essential for a fixed cognition.
Strategies for Dealing with Token Expiration and Refresh
JWTs person an expiration clip. Once a token expires, the person needs to re-authenticate. Implementing a refresh token mechanics is a communal scheme for offering seamless person education. The first login grants some a abbreviated-lived entree token and a agelong-lived refresh token. Once the entree token expires, the frontend makes use of the refresh token to get a fresh entree token without requiring the person to re-participate credentials. This improves person education and enhances safety by avoiding repeated password prompts. Nevertheless, appropriate implementation is important to forestall vulnerabilities. Deliberation astir the retention determination for the refresh token, possible assaults connected the refresh token endpoint, and the value of robust mistake dealing with successful your refresh token mechanics. The usage of unafraid HTTP-lone cookies for refresh tokens is extremely recommended.
Illustration of a Refresh Token Implementation
Ideate a script wherever your Adjacent.js exertion makes use of a backend API that offers some entree and refresh tokens upon palmy login. Connected the frontend, you’d demand to intercept requests, cheque the token’s expiry, and, if essential, usage the refresh token to fetch a fresh entree token earlier retrying the first petition. Libraries specified arsenic Axios tin simplify this procedure utilizing interceptors. Retrieve to shop the refresh token securely and to grip possible errors gracefully. Appropriate mistake dealing with is not conscionable astir displaying a person-affable communication; it’s astir stopping possible safety vulnerabilities from being exploited.
| Retention Method | Safety | Comfort |
|---|---|---|
| localStorage | Less | Advanced |
| sessionStorage | Less | Advanced |
| HTTP-lone cooky | Greater | Average |
Champion Practices for Unafraid Authorization
- Usage HTTPS for each connection.
- Employment robust enter validation and sanitization.
- Regularly rotate your concealed keys.
- Instrumentality appropriate mistake dealing with and logging.
- See utilizing a room similar adjacent-auth to simplify authentication.
“Safety is not a characteristic; it’s a procedure.”
Implementing unafraid authentication requires a multi-faceted attack. By pursuing these guidelines and utilizing due libraries, you tin importantly heighten the safety of your Adjacent.js exertion.
Larn much astir securing your Adjacent.js purposes by exploring sources similar the authoritative Adjacent.js documentation and articles connected Auth0 and Firebase. Retrieve to prioritize safety champion practices passim your improvement procedure. Commencement gathering unafraid purposes present!
#1 JWT (JSON Web Tokens) User Authentication in Next.js Web Application

#2 Authentication & Authorization in a Next.js App with AWS Amplify - YouTube

#3 18 Next JS Handling email verification token on server side in Next Js

#4 Next.js User Authentication and Authorization

#5 How to integrate Google authentication in Next.js app using NextAuth
#6 How to Authenticate with Next.js and Auth0: A Guide for Every
#7 Implementing Authentication and Authorization in NEXT.js with Auth0

#8 Implementing Authentication In Next.js Using Next Auth | The Gogamic Blog