Figuring out the origin of a keystroke successful Python tin beryllium important for assorted purposes, from safety monitoring to automated investigating. This procedure, nevertheless, isn’t straightforward and requires knowing the underlying working scheme mechanisms and Python’s capabilities for interacting with them. This weblog station volition delve into the methods and challenges active successful pinpointing the direct procedure liable for a fixed keystroke case connected a Home windows scheme.
Figuring out the Root of Keystrokes connected Home windows
Monitoring behind the exact procedure that initiated a keystroke case connected Home windows entails leveraging the Home windows API done Python. This requires a heavy knowing of however keyboard enter is dealt with by the working scheme. Straight accessing debased-flat keyboard occasions allows for granular power and recognition, but it besides necessitates cautious dealing with of possible errors and scheme-flat limitations. The complexity increases once dealing with aggregate functions simultaneously interacting with the keyboard.
Using the pynput Room for Keyboard Monitoring
The pynput room offers a relatively advanced-flat interface for monitoring keyboard enter. Piece it doesn’t straight place the originating procedure, it gives a starting component for capturing cardinal occasions. By combining pynput with another scheme monitoring instruments, you tin possibly correlate occasions and deduce the origin. Nevertheless, this method unsocial mightiness not message the precision required for analyzable scenarios. Further probe into the procedure ID (PID) related with the case turns into essential.
Precocious Strategies: Procedure ID Correlation and Debased-Flat Entree
For much close recognition, you demand to decision past pynput and prosecute with less-flat Home windows APIs. This typically includes utilizing libraries similar ctypes to work together with features similar GetForegroundWindow and GetWindowThreadProcessId. By acquiring the foreground framework and its related procedure ID, you tin possibly nexus keystrokes to circumstantial processes, especially if the keystrokes are straight related with person action with that framework. Nevertheless, this attack has limitations, especially with inheritance processes oregon functions not straight interacting with the focused framework.
Challenges and Limitations
Precisely figuring out the root of all keystroke presents respective challenges. Any purposes inject keystrokes into the scheme without being the foreground framework. Others mightiness usage keyboard hooks oregon another strategies to obscure their actions. Furthermore, dealing with aggregate processes simultaneously interacting with the keyboard tin pb to analyzable scenarios that necessitate blase investigation and possibly heuristics to find the about possible origin. It’s important to beryllium alert of these limitations earlier attempting specified a project.
Array: Evaluating Antithetic Approaches for Keystroke Recognition
| Method | Precision | Complexity | Libraries Required |
|---|---|---|---|
pynput |
Debased | Debased | pynput |
Home windows API (ctypes) |
Average-Advanced | Advanced | ctypes |
Decision: Navigating the Complexities of Keystroke Attribution
Figuring out the exact procedure liable for sending a keystroke successful Python requires cautious readying and possibly precocious programming strategies. Piece libraries similar pynput message a starting component, they mightiness not ever suffice. For much exact outcomes, interacting straight with the Home windows API is essential, although it importantly increases the complexity. Retrieve to seek the advice of the documentation for ctypes and pynput and to grip possible errors appropriately. Knowing the limitations of all attack is important to mounting practical expectations.
Further investigation into Home windows keyboard hooks and precocious scheme monitoring strategies mightiness beryllium essential for precise analyzable scenarios. Retrieve ever to regard person privateness and adhere to ethical guidelines once dealing with keystroke monitoring. For much successful-extent accusation connected Home windows API features, mention to the authoritative Microsoft documentation: Microsoft Home windows API Documentation.
#1 Simulate Key Presses in Python

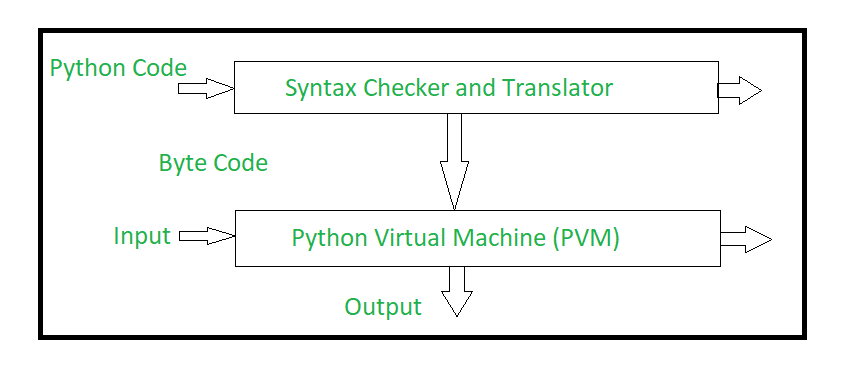
#2 Internal working of Python - GeeksforGeeks
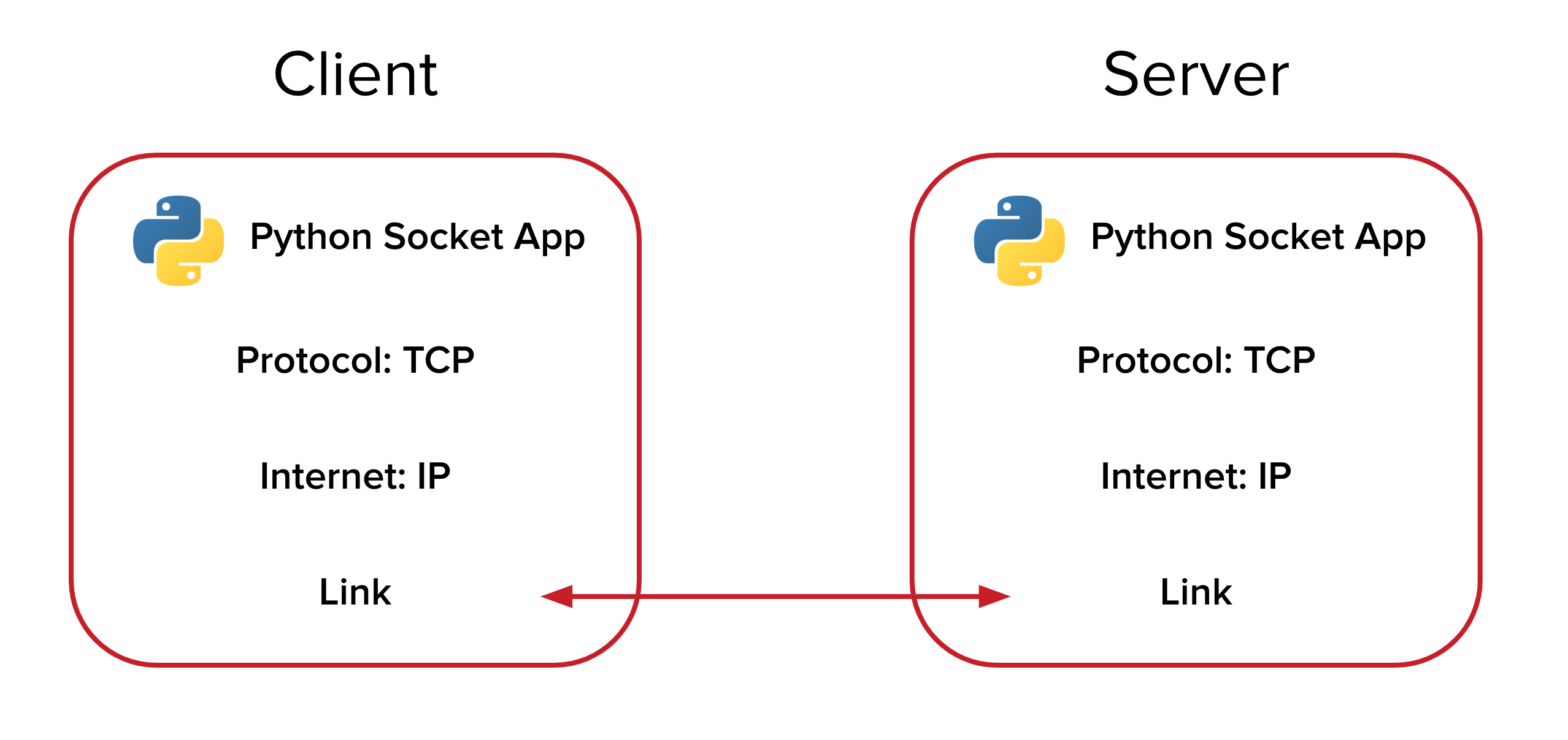
#3 Socket Programming in Python: Client, Server, Peer | PubNub - EU
#4 Parameters Python
#5 Python Coding- Encrypted Client/Server TCP Communication

#6 A Simple Python Callback Handler Example Help Center
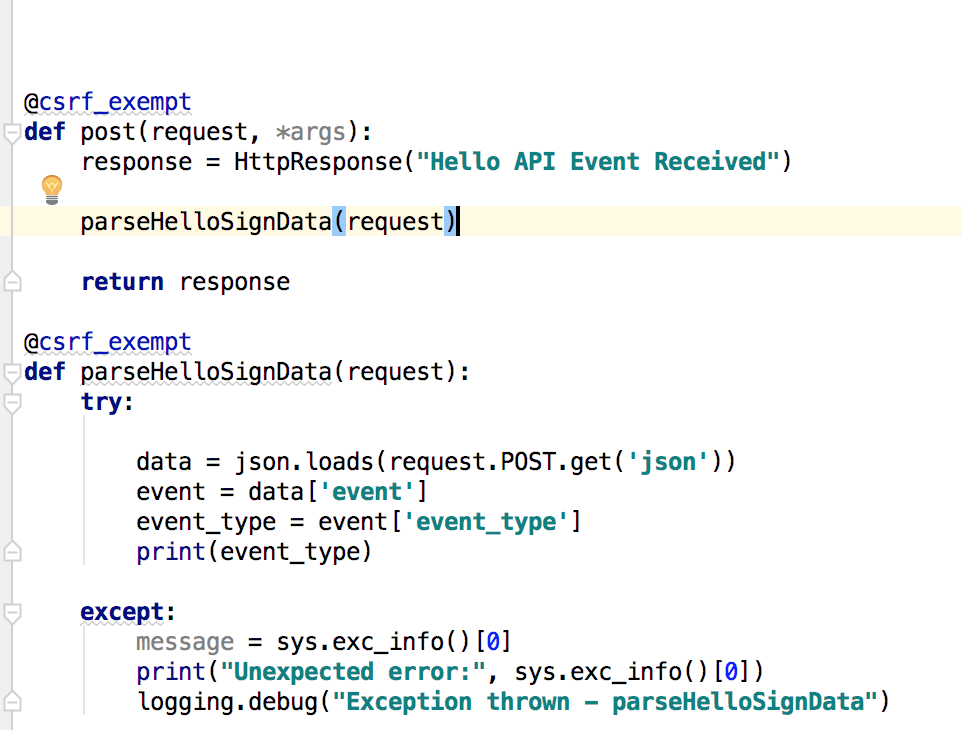
#7 Text File Handling in Python Handout - CS-IP-Learning-Hub

#8 Figure 1 from Keystroke Level Modeling as a Cost Justification Tool
